.webp)
SPF, DKIM & DMARC: How to keep your cold emails out of spam
Cold emails aren’t always failing, but many of them are simply unseen. Every day, millions of carefully written outreach messages disappear before they even reach an inbox.
The reason usually isn’t poor copy, it’s a missing layer of technical authentication most senders have never heard of.
Here’s the reality: major providers like Gmail and Yahoo now block or filter out bulk emails that aren’t verified. Without proper SPF, DKIM, and DMARC records in place, as many as 1 in 6 cold emails never make it past the gatekeepers.
The numbers are already stacked against senders. Cold email deliverability has had many new challenges over the past year as major providers rolled out stricter authentication requirements and more aggressive filtering.
The irony: many senders unknowingly make things worse by using tracking pixels to monitor opens - a practice that often triggers the very spam filters they're trying to avoid.
That is why we focus on authentication before any outreach begins. Making sure your domains are correctly set up with SPF, DKIM, and DMARC is the foundation for keeping campaigns out of spam and in front of the right people.
And today we’ll break down these protocols, explain how they work together, and show you how to keep your cold emails landing where they belong – the inbox.
What are SPF, DKIM & DMARC and why your cold emails need them
When you send a cold email, the receiving server doesn’t just look at your message; it first checks if it can trust where that email came from.
This is where SPF, DKIM, and DMARC step in. Without them, your outreach looks questionable, and more often than not, it ends up flagged or filtered out.
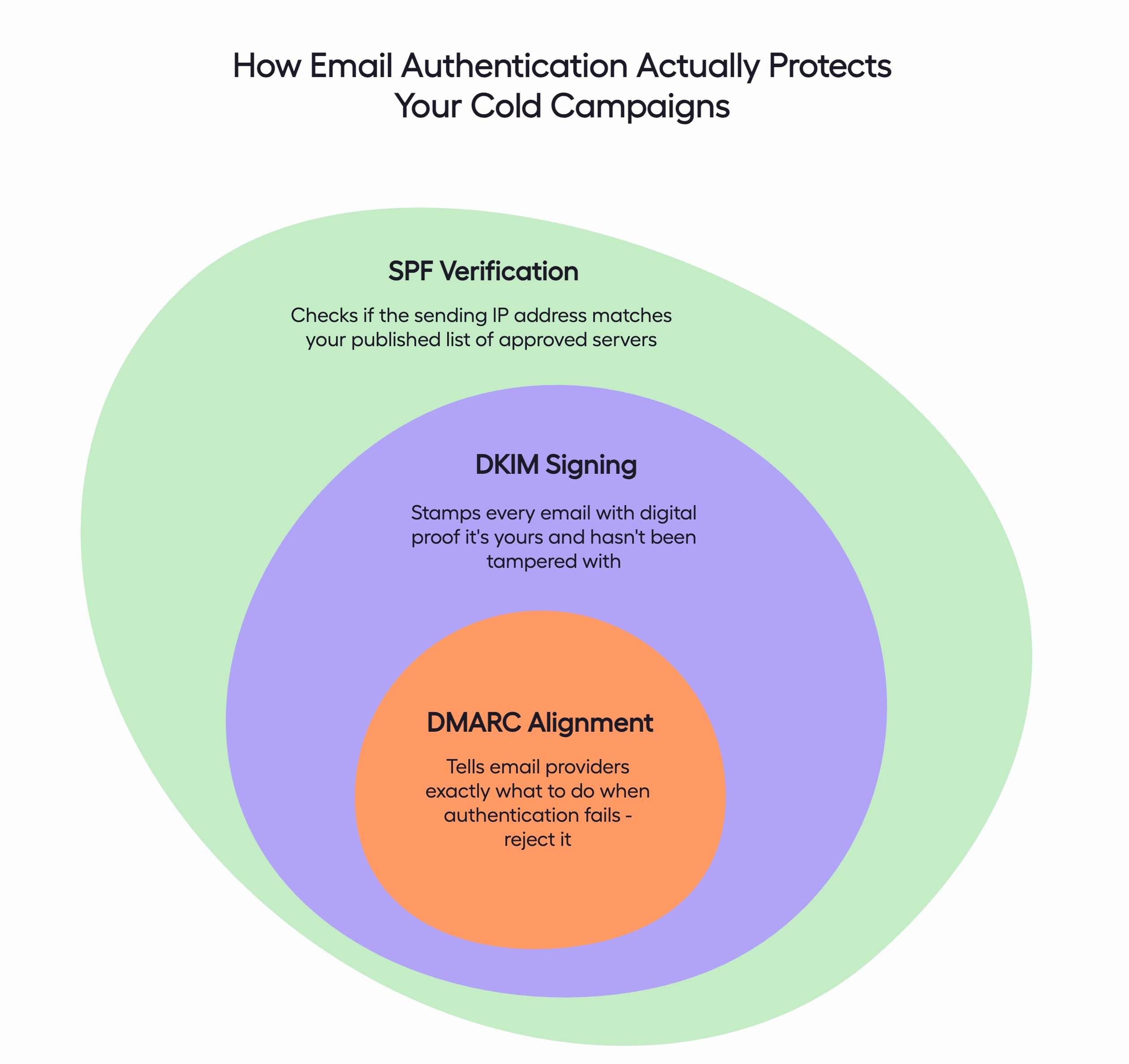
- SPF (Sender Policy Framework) is the first layer.
It’s a record that tells email providers which servers are allowed to send on your behalf. If Gmail gets a message from your domain, SPF helps confirm it was sent from an approved source instead of a spammer pretending to be you.
- From there, DKIM (DomainKeys Identified Mail) adds another layer of security.
Think of it as a digital signature stamped onto every email. It proves the content hasn’t been tampered with during delivery and that it genuinely belongs to your domain.
- Finally, DMARC (Domain-based Message Authentication, Reporting, and Conformance) brings everything together.
It decides what happens if an email fails those checks – whether it gets blocked, lands in spam, or slips through with a warning.
How SPF, DKIM & DMARC directly impact your cold email deliverability rates
Numbers tell the story clearly. Email authentication has a direct impact on whether your cold emails make it to the inbox or get dumped into spam.
When Google and Yahoo rolled out stricter requirements in early 2024, they reported a 65% drop in unauthenticated emails hitting inboxes. That wasn’t because fewer emails were being sent – it was because unauthenticated ones were being blocked.
Without proper setup, your cold emails face three common fates:
- Flat-out rejection at the server level before anyone ever sees them.
- Spam folder exile, where open rates sink close to zero.
- Reputation damage, as failed emails and spam complaints hurt your domain, making it even harder to reach inboxes in the future.
The upside of fixing authentication is measurable.
Senders who adopt strict DMARC enforcement often see up to 10% better inbox placement, especially when combined with cold email deliverability best practices that strengthen reputation over time.
For a campaign targeting 10,000 prospects, that’s an extra 1,000 emails actually being seen. Those additional impressions can mean more meetings booked and more deals closed.
There’s also a compounding effect.
Once your emails consistently pass SPF, DKIM, and DMARC checks, providers begin to treat your domain more favorably. Better deliverability improves engagement rates, which signals to inbox providers that your emails are wanted, which in turn strengthens future deliverability.
The role of SPF in getting your cold emails past spam filters
SPF is your first line of defense against spoofing.
It prevents outsiders from pretending to send emails from your domain by publishing a public list of approved sending sources. If a server isn’t on the list, the message raises an instant red flag.
For cold email, SPF mistakes can ruin entire campaigns. Which is why many companies lean on a expert cold email lead gen agency to manage authentication alongside outreach.
If you’re using an outreach tool or SMTP service that isn’t added to your SPF record, every single message fails authentication. Gmail treats these failures as a major spam indicator, especially in bulk sending patterns.
The fix is simple but critical:
- Add a single DNS TXT record that lists all authorized sending sources.
- Make sure every platform you use is included.
- Double-check regularly when adding new tools.
You can only have one SPF record. If you publish multiple, you’ll break authentication entirely, and fixing the mess can take weeks.
What DKIM does to protect your cold email messages (and your reputation)
SPF covers who’s allowed to send, but DKIM covers the integrity of your message. Each email gets a cryptographic signature that proves it came from your domain and wasn’t altered in transit.
Unlike SPF, DKIM still works if your message is forwarded, which makes it especially valuable for maintaining strong cold email deliverability even in complex sending scenarios.
Email providers weigh DKIM signatures heavily when deciding inbox placement. A missing DKIM signature on bulk sends is almost guaranteed to push your cold outreach into spam.
For senders who rely on shared infrastructure, DKIM also builds a domain-specific reputation that follows you regardless of IP addresses.
How DMARC protects your cold email campaigns
DMARC is the policy layer that connects SPF and DKIM and makes the rules enforceable. It tells receiving servers what to do when an email fails authentication: quarantine it, reject it, or allow it through under watch.
Without DMARC, passing SPF or DKIM is helpful, but not decisive.
.webp)
SPF, DKIM & DMARC vs general spam filters: What each actually influences
Email deliverability isn’t decided by one single factor, and even if you’ve mastered how to write the best cold email, your outreach will still fail without authentication.
Authentication and content filtering both play their part, but they solve very different problems. So knowing the difference helps you build campaigns that clear both hurdles.
Here’s how the two layers compare:
What SPF, DKIM, and DMARC actually control
Authentication protocols deal purely with technical trust. They don’t care about your subject line or whether your copy sounds human. Their job is to prove you are who you say you are and that your message hasn’t been altered.
- SPF: Verifies the sending server’s IP address is authorized by your domain.
- DKIM: Confirms the message content and headers weren’t modified in transit.
- DMARC: Enforces alignment and tells receiving servers what to do with failed checks.
These checks happen before anything else. If they fail, the content of your email doesn’t even get a chance to be reviewed.
What spam filters look at (beyond authentication)
Once authentication clears, spam filters take over. They run a much deeper analysis focused on behavior, content, and engagement.
.webp)
How authentication and content work together
Authentication without good content is like having the right ID but acting suspicious – you’ll pass the first gate only to be flagged later, which is how many email deliverability issues start.”
We’ve seen campaigns with flawless SPF, DKIM, and DMARC setups still fail because of weak copy or high spam complaints. On the flip side, polished content won’t save a campaign if the domain fails basic authentication.
The best cold email strategies nail both sides:
- Authentication ensures providers trust your domain and track your reputation fairly.
- Content and engagement keep that reputation positive and improve inbox placement over time.
So remember, cold email success comes from combining technical trust with strong messaging and knowing how to write a cold email that resonates with real people. Neglect either side, and you’re handing providers a reason to block you.
How to set up SPF DKIM and DMARC for cold outreach
Email authentication isn’t complicated, but it does need to be set up in the right order. A sloppy or incomplete setup can undo your entire outreach effort.
The process works best when you approach it methodically: SPF first, DKIM second, DMARC last.
The right way to set up SPF
SPF is all about making sure only the right servers are allowed to send from your domain (a quick tip from us: pairing authentication with email warmup tools helps build early trust and smooth deliverability as you scale).
For cold outreach, that means building a complete list of every service that touches your emails:
- Your primary email provider (Google Workspace, Microsoft 365, etc.)
- Cold outreach platforms you’re actively using
- Any SMTP services or relay providers
- Tracking or bounce-handling tools
The SPF record is a simple DNS TXT entry that starts with v=spf1. From there, you’ll add “include” statements for each provider, like include:_spf.google.com for Google or include:spf.protection.outlook.com for Microsoft. Cold email tools supply their own include values as well.
How to configure DKIM so every cold email gets properly signed
DKIM adds a digital signature to each message, proving it came from your domain and wasn’t altered on the way. Setting it up varies by provider but follows the same pattern:
- Generate 2048-bit RSA keys (stronger than outdated 1024-bit defaults).
- Publish the public key as a TXT record in DNS.
- Use clear selector names (e.g., “google” for Workspace or “outreach2024” for your cold email tool).
Providers handle it slightly differently:
- Google Workspace: enable DKIM in the admin console.
- Microsoft 365: publish CNAME records pointing to their DKIM keys.
- Cold email tools: provide their own selectors and instructions.
Multiple DKIM keys can coexist under one domain, so your main inbox and outreach system can sign with different selectors.
Test DKIM by sending emails to various providers and checking headers. Look for “dkim=pass.” If you see failures, common culprits are DNS delays, formatting errors, or the service not signing mail properly.
DMARC implementation: The final layer of protection
DMARC ties everything together by setting rules for what happens when SPF or DKIM fails.
- Start with p=none so you can monitor without blocking mail.
- Send reports to an address you’ll actually check – they contain valuable data about which sources are authenticating correctly.
- Watch the reports for a few weeks to spot forgotten services or misconfigurations.
Once confident, step up enforcement:
- Move to quarantine so failing emails hit spam instead of disappearing.
- Shift to reject only after your legitimate mail is consistently passing.
Remember that DMARC alignment matters. The “From” domain must align with either SPF or DKIM. Default relaxed alignment allows subdomains, while strict alignment requires exact matches.
How to verify your SPF DKIM, and DMARC setup is actually protecting your emails
Setting up authentication is only step one. To know it’s actually working, you need proof that your cold emails are passing checks, reaching inboxes, and blocking unauthorized senders. Verification is what separates “configured” from “protected.”
Start with DMARC aggregate reports.
These daily reports show how many emails pass or fail across different providers. Don’t try to decode raw XML – use a parsing tool or service that turns the data into dashboards. Look for:
- Authentication success rates across providers
- Unauthorized sending attempts
- Legitimate systems that are still failing checks
Next, track inbox placement.
Tools like GlockApps or Inbox Insight reveal where your messages actually land – whether that’s inbox, spam, or promotions. Compare results before and after authentication. A proper setup should noticeably increase inbox percentages, especially if your domain struggled with deliverability before.
Ongoing monitoring is just as important. Many DMARC services let you set alerts that flag unauthorized senders or sudden drops in pass rates. Catching issues early prevents them from snowballing into serious reputation problems.
When something does fail, here’s where to look first:
- SPF failures often mean a missing include or unauthorized IP.
- DKIM failures usually come from DNS propagation delays, formatting mistakes, or services not signing properly.
- DMARC failures with SPF or DKIM passing usually point to alignment problems – the “From” domain isn’t matching the authenticated domain.
- Widespread failures across multiple systems suggest a DNS publishing or propagation issue.
What to do when authentication tests fail
Failures happen, and they usually trace back to specific, fixable causes:
.webp)
And don’t just fix and forget. Anytime you change sending platforms, update DNS, or add new tools, re-run your verification process to make sure your authentication setup stays airtight.
Final thoughts
Okay, we’ve covered a lot. You now know that SPF, DKIM, and DMARC aren’t just acronyms – they’re the foundation that decides whether your cold emails reach the inbox or get lost in spam. Without them, even the best-written outreach never stands a chance.
The payoff is real and measurable.
Campaigns often see 20–50% improvements in inbox placement once authentication is properly set up. That means more prospects opening, more replies coming in, and more deals moving forward – all without sending a single extra email.
And the benefits don’t stop there. Authentication also future-proofs your outreach. As providers keep tightening the rules, the senders who adapt will keep landing in inboxes while everyone else slowly disappears from view.
Here’s the bottom line:
- Authentication stops spoofing before it damages your brand.
- It lifts engagement rates by keeping your emails where they belong.
- It builds long-term trust with providers who track domain history.
- It unlocks growth by letting your prospects actually see your message.
This is exactly why we’ve helped hundreds of B2B teams fix their authentication setups and rescue campaigns that were dying in spam. The difference wasn’t better copy, clever subject lines, or fancy automation.
It was simply making sure their emails could be delivered.
So if you need help with setting up SPF, DKIM, and DMARC – or simply want peace of mind that your emails are actually reaching the people you worked hard to target – our team knows the pitfalls, the shortcuts, and the best practices that make cold outreach land where it should: the inbox.
Remember: prospects can’t reply to an email they never received. Authentication makes sure they do.
Frequently asked questions
SPF, DKIM, and DMARC are email authentication protocols that prove you are a legitimate sender. SPF authorizes which servers can send from your domain, DKIM adds a cryptographic signature to prevent tampering, and DMARC enforces alignment between your “From” domain and the authentication results. For cold outreach, these protocols are critical because providers like Gmail and Yahoo now require authentication for bulk sending. Without them, up to 17% of emails may be filtered before they ever reach a prospect’s inbox.
Start with SPF by publishing a TXT record in your DNS that includes all the services sending on your behalf, such as Google Workspace, SMTP relays, or cold outreach tools. Next, enable DKIM signing in each platform you use and publish the public keys in DNS. Finally, set up DMARC starting with policy “none” to monitor, then move to “quarantine” and eventually “reject” once you’re confident all legitimate emails are passing. Each stage should be tested thoroughly to avoid breaking deliverability.
Authentication makes a big difference, but it isn’t a magic shield. SPF, DKIM, and DMARC cover the technical trust layer, ensuring you’re recognized as a valid sender. However, spam filters still evaluate other signals such as your content, sending frequency, and engagement levels. Authenticated domains often see inbox rates improve by up to 10%, while non-authenticated domains risk rejection before even hitting spam. In short, authentication is essential, but content and sending behavior still matter.
The biggest pitfalls include publishing multiple SPF records instead of one, forgetting to include all sending sources in your SPF record, and relying on weak 1024-bit DKIM keys instead of stronger 2048-bit ones. Another common mistake is enforcing a DMARC “reject” policy too quickly without first monitoring reports. Many senders also miss domain alignment, where the visible “From” address must match the domains authenticated by SPF or DKIM. Always test thoroughly and review DMARC reports regularly to catch problems early.
Don’t miss these
Get your first lead this month
14 days to get started. 7 days to get your first lead on average.






.webp)
.webp)


.webp)